The S in Spotify stands for Song – not Security.
 Ignoring the second commandment: Thou shalt not implement broken authentication.
Ignoring the second commandment: Thou shalt not implement broken authentication.
Boulevard of broken dreams
Spotify is the largest and most popular audio streaming subscription service in the world, with an estimated 300 million users. The «Spotify model» is regarded as a successful approach to scaling agile to large organizations. Published in a paper in 2012, it draws on the «Scrum» methodology and focuses on culture and introduces concepts such as «squad», «chapter» and «guild». Many companies have since adopted the «Spotify model» for its promise to increase innovation and productivity.
Spotify was during the summer of 2020 a victim of a large information disclosure incident where up to 350 000 accounts were compromised. A huge database of usernames and passwords obtained from an unknown source was used to target Spotify accounts.
If I could turn back time
Similar to a 2019 incident reported in New York Times, Spotify users started having playback interrupted, their music playlists deleted, and unknown devices with pictures of strangers added to their accounts. Fraudsters could use the stolen credentials to access a user’s account and take advantage of digital services paid for by the original user (such as Spotify Premium). Fraudsters could also use the contact information to directly target the exposed users with phishing emails, tricking them into providing sensitive data like credit card details, or clicking a fake link embedded with malware. By imitating Spotify in these emails, they could be very successful in such a campaign.
You give love a bad name
The Open Web Application Security Project (OWASP) is a well-regarded, online non-profit community that produces technology best practice in the field of web application security. While not responsible for the original leak, Spotify has for a long time failed to protect its users' data in 2 important ways, both addressed by the second on the list of OWASP Top 10 Web Application Security Risks:
First, Spotify failed to detect and prevent brute force login attempts. Limiting, delaying, and alerting failed login attempts would most likely have rendered such an attack unsuccessful.
Secondly, Spotify did not (and as of the time of writing, still do not) support native multi-factor authentication (MFA). Native MFA has yet to make it into the Spotify offering, despite having been requested by numerous Spotify users dating all the way back to 2015. MFA would most likely have prevented the automated, credential stuffing attack Spotify was a target of. It should be noted that Spotify does support login with Facebook which offers MFA, but at the same time comes with its own set of tracking and privacy concerns.
You are not alone
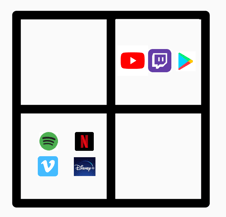
Figure 1 – Magic multi factor authentication (MFA) quadrant - Top right sites do support MFA, bottom left do not.
Media platforms such as YouTube, Twitch and Google Play all support MFA. On the dark side, Spotify is far from alone in the entertainment business not supporting MFA: Neither of Netflix, Disney+ and Vimeo offer such support at the time of writing. The rationale for not putting this feature into the market, which when properly implemented would allow users to protect themselves even when the service does not, is beyond comprehension.
Modern frameworks such as OKR, Agile and Scrum focus on outcomes and business value and center less on risk and security. Improving cyber security can enhance customer loyalty and trust, and enhance reputation in the market, making it a key competitive differentiator.
Learning to fly
Don´t forget to secure your deliveries, whether you embrace the Spotify model or not. Consulting the OWASP community and its´ resources is an excellent starting point.
The S in Spotify stands for Song – not Security.

